The #1 Just In Time Identity Protection
Our company is dedicated to providing the most secure identity access and authorization solutions available for your entire organization.
Rapid Integration with all leading identity platforms





Native language api integration





Why choose Next Level3?
When you signup to Next Level3 you get access to our complete SaaS offering including Passwordless MFA, Realtime Policy control and cutting edge permission & approval management.
More importantly you will get comprehensive identity security protection that is faster to rollout, more affordable to use and easier to maintain.

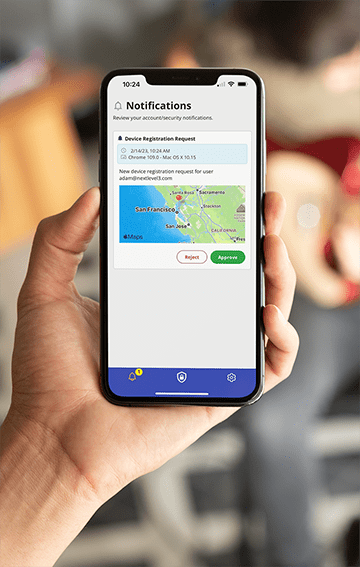
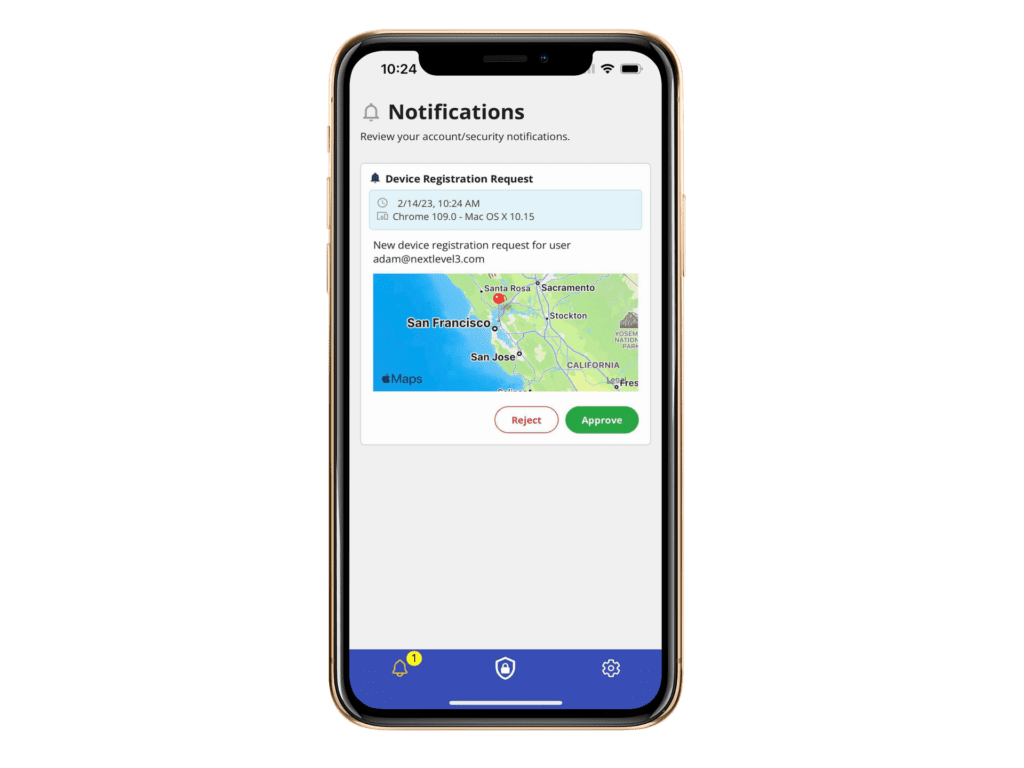
JIT Access
Passwordless Identity seamlessly connected to your existing identity infrastructure.

JIT Policies
Redefine account control for your organization solving critical internal use cases.

JIT Approvals
Enable customized approvals for any application action preventing fraud and extending biometric protections into your application use cases.
Just In Time enables effective Zero Trust
JIT Access provides the biometric protections you want. JIT Policies allow you to define when users should get access and JIT Approvals lets you redefine how permissions and approvals work within your organization in real time.
Prevent multiple current attack vectors
Obtain Compliance
Discover the full potential of JIT Access how it can help you prevent most of the top attack vectors while achieving compliance with Industry leading Cyber Insurance providers.
It's Passwordless and more...
JIT Access provides proven passwordless protection to all your applications, endpoints and network connections.
Increase your protection using JIT Policies and JIT Approvals to prevent a multitude of external and internal attack scenarios.