#JIT Policies - Effective Auditable Control
Experience automated policies that enable effective controls, reduce ongoing maintenance and reduce costs.
Prevent multiple current attack vectors
Obtain Compliance
Discover the full potential of JIT Policies and how it can help you prevent most of the top attack vectors while achieving compliance with Industry leading Cyber Insurance providers.
How it works
JIT Policies enable you to steam line access to applications, endpoints and your network through effective policies.
You can predefine or integrate policies natively into your own applications with our API’s for dynamic control throughout your application stack.
Choose from a variety of policy types to control access for a variety of scenarios.
- Remote workforce device lockout
- Employee Onboarding/Offboarding
- Prevent Lateral Movement
- Scheduled access control
- Location based access control
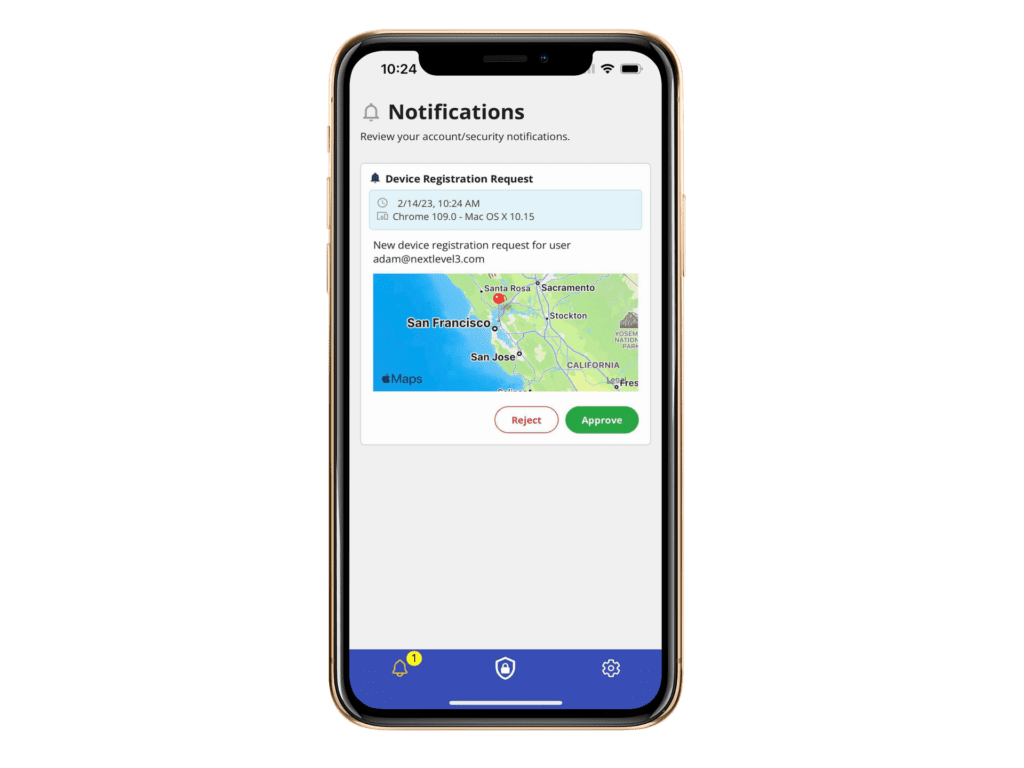
Next Level3 does more! Extend your protection using JIT Access and JIT Approvals to prevent a multitude of external and internal attack scenarios.

Automatic push attack aware protection without codes





Use your existing mobile or web FIDO2 supported devices





Why choose Next Level3?

JIT Access
Passwordless Identity seamlessly connected to your existing identity infrastructure.

JIT Policies
Redefine account control for your organization solving critical internal use cases.

JIT Approvals
Enable customized approvals for any application action preventing fraud and extending biometric protections into your application use cases.