From zero trust and passwordless solutions to unphishable MFA, SDPs, and 5G security – there are a lot of options to enhance your tech stack.
Security concerns plaguing CISOs and other C-suite officers haven’t changed in ages despite the evolution of cybersecurity trends — they’ve just gotten more frequent and rear their heads in more places.
With “50% more attack attempts per week on corporate networks globally in 2021” compared to 2020, there’s no rest for the weary. Attack surfaces are growing, briefing meetings seem constant, and yet it’s increasingly difficult to get buy-in to expand dev sec ops toolkits.
Non-tech leadership is tired of hearing about security procedures and problems, but this is a CISO’s daily worry. Hacker groups like Nobelium aren’t getting tired, though – they’re just getting started. Hackers view every new trend as a unique challenge to be solved and spare no expense or resource to find a way around it.
As you look to the future of advancing your tech stack, here are some of the top cybersecurity trends to consider.
Zero trust strategy
One of the hottest buzzwords in the industry recently is “zero trust.” Everyone is talking about the importance of implementing zero trust strategies, but not as many are actually doing it.
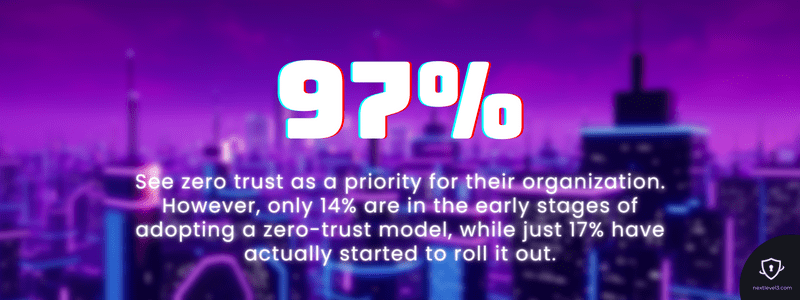
A Banyan survey showed that CISOs certainly have zero trust on their minds as “97% see zero trust as a priority for their organization. However, only 14% are in the early stages of adopting a zero-trust model, while just 17% have actually started to roll it out.”
This delay is not because they don’t think it’s important but because it’s not as simple as buying a new product or creating a single response plan. Zero trust is a cybersecurity philosophy. As Joseph Carson says, “Organizations do not become a zero trust shop. They practice a zero trust mindset.”
So, what is a zero trust mindset? The cornerstone is that nobody and no devices are trusted by default. A trust-no-one attitude shifts the old saying from “trust, but verify” to “never trust and always verify.” The goal of zero trust is not to look at “good guys” as “bad guys” but rather to minimize loss by catching breaches sooner rather than later through required verification.
This means things like:
Continuously authenticating identity
Continuously authenticating devices with MFA
Making access purely need-to-know
Siloing data with smaller perimeters
Continuously monitoring for threats
Automating responses when computers are faster than humans
We will inevitably see the rise of more concrete cybersecurity trends and tools that align with the zero trust mindset, as well.
Passwordless solutions
We all know passwords are one of the weakest points in a security system because of how people use and reuse them. According to Verizon’s 2021 Data Breach Investigations Report (DBIR), credential vulnerabilities account for over 84% of all data breaches. In theory, passwordless solutions can increase security while also offering a smoother user experience — a real win for those of us who tend to see an inverse relationship between security and convenience.
Another benefit of passwordless authentication is it can simplify IT operations. Without having to manage and reset passwords, help desks and users will save both time and resources.
There are many options to remove the friction of passwords, and some are better than others:
Proximity badges
Physical tokens like FIDO USB keys
Software tokens or certificates
Magic links
Biometric scanning and recognition
Authentication apps
These can take time to configure and implement, especially when combining several for MFA. Hopefully, you also have a plan in place to address this. Cyber insurance companies are considering making it a requirement to have an unphishable MFA solution in place before underwriting policies.
Unphishable MFA
2FA and MFA have been around for a while, but phishing has been a problem for just as long. Today, it’s crucial to have authentication that cannot be intercepted. Email 2FA, SMS, security questions, and even magic links are notorious for becoming breach targets since they’re not difficult to intercept. In other words, MFA alone isn’t enough.
The US government even released a memo in January of 2022 promoting zero trust strategies and providing a roadmap for phishing-resistant MFA in all federal agencies by the end of 2024. These evolutions in cybersecurity standards are sorely needed, and organizations that rely solely on MFA are insufficiently protected.
Unphishable MFAs move from knowledge-based credentialing to possession-based. Make your MFA unphishable by using more advanced FIDO-compliant authentications like:
Biometrics
Cryptographic keys
Physical tokens
Hardware and device proximity checks
By changing the authentication flow, and using multi-device, passwordless FIDO-compliant logins for users, you can extend the capabilities and strength of existing MFA solutions.
Software-defined perimeters (SDPs)
CISOs also recognize that SDPs supersede VPNs. Software-defined perimeters hide infrastructure like servers and routers so they cannot be seen. Each authenticated user is given a unique connection with access to only necessary services and data.
VPN alone gives all logged-in users access to the whole network, making it vulnerable if credentials are stolen. It can also be more challenging to identify breaches because the user’s identity has not been verified if credentials are shared or stolen.
An SDP can simplify access management as well. Multiple VPNs need to be created for every level of access, while everything within that VPN remains vulnerable. This creates complexity for IT staff to manage multiple VPNs and keep track of which users have access to each one.
SDPs and VPNs can increase security when used together, though in some cases, SDPs can replace VPNs. The authentication process with an SDP:
Verifies the user’s identity
Confirms the device being used
Creates a secure, individual network
Grants only minimum network access
Provides the user access to hidden resources through an encrypted network
Because SDPs don’t share network connections, they reduce attack surfaces. They’re also location- and infrastructure-agnostic, making remote teams easier to manage and keep secure.
5G Security
The rapidly increased use of 5G networks and devices has also increased the need for robust 5G security measures. Any security-minded person understands that legacy security solutions “are just not fast enough or adaptive enough to protect the whole of 5G against cyberattacks, while also supporting performance and digital innovation.”
5G increases data speed and volume, the number of connected devices, and the geography where networks are accessible. This increases the attack surface of an entity to an overwhelming degree. Plus, 5G networks can be both public and private, complicating matters even more.
As businesses more widely adopt 5G, CISOs, CTOs, and CIOs will have to shoulder increased responsibility. Pablo Molinero, Senior Director of Product Management for Telcos at Fortinet, shares that it’s critical to have:
- Microsegmentation
Quickly and regularly updated devices
Low-latency solutions
Durable devices and equipment for all types of physical environments
Staying aware of cybersecurity trends
No CISO needs to be told the importance of keeping on top of essential and fast-evolving cybersecurity trends. You likely already know that zero trust is a massive step in most organizations’ security planning. Perhaps you’re even implementing some form of passwordless solutions already – even if it’s just single-device and not yet multi-device.
Although it’s becoming increasingly complex to plan and implement security measures for any organization, adopting the right ones is extremely urgent. With more info in the world being shared at faster speeds, security is getting harder to maintain, and more considerations must be taken into account — especially if you want to reduce future risk and stay compliant with evolving cyber insurance standards.
