How can we solve for advanced threats like biometric MFA bypass, phishing/smishing, software supply chain attacks, MitM attacks, and credential stuffing?
Most of today’s most prolific cybersecurity threats don’t strictly happen due to technology vulnerabilities.
Software and hardware shortcomings are undoubtedly essential to consider when creating a solid security plan, but often, human vulnerabilities are the obvious route for a breach – and social engineering enables many types of cyber attacks.
The top cybersecurity threats have both human and tech elements that you should consider. Social engineering is how attackers target user vulnerabilities, and, according to an FBI Internet Crime Complaint Center (IC3) PSA reporting on 241,206 attack incidents in the second half of 2021, “Combined domestic and international losses incurred amounted to the US $43.31 billion.”
Training personnel and implementing the right technological prevention and response measures should be combined to secure your company’s information.
Phishing and smishing
One of the most common types of cyber attacks are phishing and smishing scams — which increased 700% in the first six months of 2021. Social engineering is the primary avenue for this type of attack because it involves convincing someone to open a link. Through email (phishing) or SMS (smishing), attackers target people by enticing them to open a malicious link and steal information.
Smishing — In text messages, package delivery notifications and “urgent” financial services alerts are widespread. The messages may urge people to “track your delivery”, “recover your account”, or “reschedule your meeting”.
Phishing — Attackers can also get sophisticated in spear phishing by emailing specific people in companies who have access to sensitive information and asking for immediate payment or urgent details. These messages can be convincing and surprisingly personal.
The best way to combat phishing and smishing cyber attacks is to educate users on using extreme caution when opening links, whether from random places or presumably trusted places like internal email thread replies.
Biometric MFA bypass
Despite many voices in the industry touting MFA solutions that include biometrics as one of the best security measures, this can sometimes become a kind of cybersecurity theater in its overstatement. Attackers are quickly learning MFA bypass tactics that even circumvent biometrics.
Biometric hacks — One bug in Windows Hello’s facial recognition system created a vulnerability that allowed USB devices to create an MFA bypass by providing stolen IR frames of someone’s face to the authentication system. Another attack on a government-run facial recognition system in China used stolen data and images to send fake tax invoices totaling 500 million yuan (US$76.2 million).

Immutable credentials — Because fingerprints and faces are in public view and cannot simply be changed, like a password, stolen biometric data becomes an extreme danger for MFA bypass. Not to mention, biometric identification is new enough that there is no universal standard when implementing it.
The widespread claim that MFA is the best solution for all potential attacks is, in many ways, cybersecurity theater which will not be well received by users once a breach occurs. In the case of biometric MFA bypass, it’s not a human error that creates a vulnerability, but human biometric data, which, if stolen, will expose users’ personal information.
Credential stuffing
While stolen passwords are more easily changed and resecured than fingerprints, faces, and voices, they’re still a huge target for cyber attacks. Because most people reuse passwords for multiple accounts, credential stuffing is low-hanging fruit for attackers and another way they exploit human vulnerabilities.
Obtaining stolen passwords for one application creates cybersecurity threats for all other services that use the same password. Attackers can quickly automate the process of trying multiple passwords on multiple applications at once.
Passwordless solutions — By using tools like proximity badges, FIDO USB keys, or software tokens, users can avoid remembering hundreds of passwords.
Continuous authentication — Assessing a user’s risk level throughout a session is how continuous authentication verifies that the credentialed user is actually the person accessing information. Instead of logging in once with a password and having unfettered access, contextual and behavioral information is used to determine the level of risk in real time.
Man-in-the-middle attacks
The explosion of remote work in the last couple of years has moved teams offsite and created huge headaches for CISOs and IT departments. More information is accessed, and more communication happens remotely, increasing the potential for man-in-the-middle (MitM) attacks.
MitM cyber attacks Intercept information between the sender and the receiver and can alter or steal it, sometimes without either party realizing. This can happen in various ways as distributed teams connect to unsecured networks, use external phone lines, and use Bluetooth in vulnerable locations.
Hijacking and spoofing — When an attacker hijacks a user’s session, they intercept information that allows them to interact with the server as that user. IP, DNS, or HTTPS spoofing creates fake versions of the former, and users interact with the spoof, serving sensitive information right to the attacker.
Wi-Fi eavesdropping — If a user connects to an unsecured network, attackers can view their activity and intercept information like logins and other sensitive data input without the user knowing.
These are just a few examples. Implementing SDP and VPN can help mitigate MitM attacks, but there’s always the critical factor of training users about what not to do when accessing networks and applications.
Software supply chain attacks
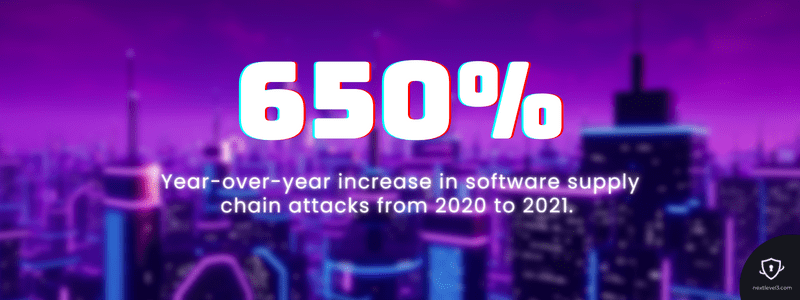
Even if you have the most comprehensive and effective security plan, vulnerabilities outside your control can be created by third-party vendors if their security is not as extensive as yours. Sonatype’s 2021 State of the Software Supply Chain report found that software supply chain attacks had a 650% year-over-year increase from 2020 to 2021.
Software gets shipped extremely fast today, often not being rigorously tested. More open-source code is also used, potentially causing much more damage since it’s spread across more applications than proprietary code.
In addition to vulnerable software development supply chains, Saas, cloud services, and APIs can be compromised, exposing your organization’s data to cyber attacks. These cybersecurity threats are minimized by thoroughly vetting vendors and code, continuous runtime security monitoring, and maintaining a zero-trust security strategy.
Cybersecurity threats will always involve people
Technology and people work together, and it’s essential to understand that cybersecurity threats are not neutralized simply by checking boxes. Training personnel and implementing cutting-edge solutions can quickly become cybersecurity theater if it doesn’t stay dynamic and iterative. Understanding how cyber attacks evolve with tech advancements should be top-of-mind for every CISO, CTO, and CIO.
