Key lessons about how the attack happened and can be avoided in the future
Even though the SolarWinds happened a couple of years ago, it’s still important today because the vulnerabilities to IT supply chain attacks and insufficient cybersecurity standards that enabled it have still not been resolved across the industry.
The devastating supply chain attack spread malicious tentacles compromising sensitive data in more than 18,000 organizations for many months before it was ever detected, causing panic across the tech world. As the industry jarringly learned, MFA standards and passwordless innovations were rendered useless because hackers were able to completely bypass them, going several layers deep in the supply chain.
In this article, we’ll look at what happened, lessons the industry is still learning, and gaps that remain in most organizations’ security tech stacks that are preventing them from identifying complex and surgically executed security breaches.
How the MFA bypass happened
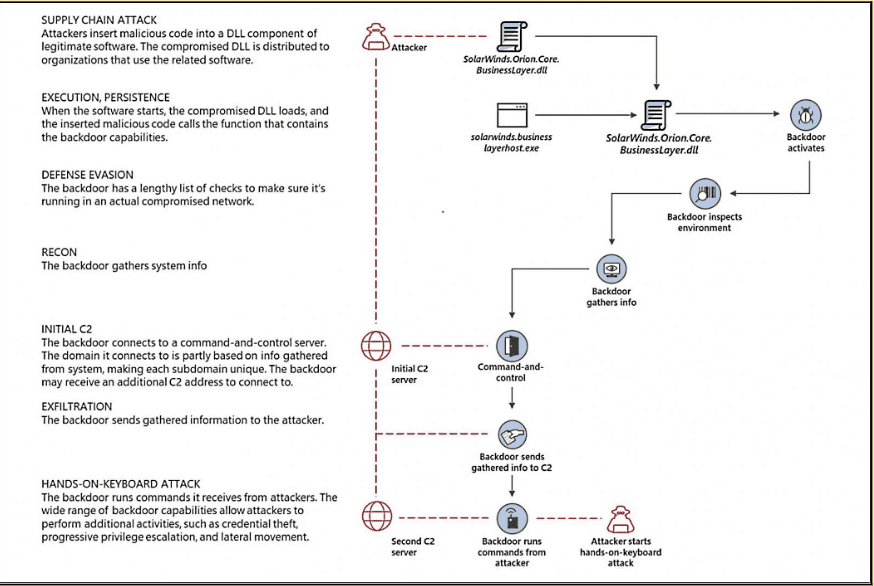
A sophisticated, state-sponsored hacking group called Nobelium executed what’s now one of the most infamous cyber attacks in history by injecting malicious code into a software update for a network monitoring tool called Orion, developed by SolarWinds.
Overview of the SolarWinds supply chain attack:
Nobelium placed malware called Sunspot into the development environment for Orion
Sunspot monitored development and replaced source files with backdoor code called Sunburst
New Orion builds with an undetected Sunburst backdoor shipped to SolarWinds clients, allowing hackers to access and gather data
Hackers collected credential information and forged SAML tokens to bypass Duo MFA and impersonate privileged users
Once they were able to forge tokens, they were able to gain verification and access accounts without triggering MFA checks
Two years later and the consequences of this attack are still not fully known because it was so stealthily deployed and multiple breaches on companies and government organizations were made with various malware strains.
MFA cybersecurity standards don’t solve supply chain attacks
Trojans completely bypass your tightest security measures
This incredibly complex trojan attack was implemented so far back in the supply chain that it was nearly impossible to detect it before reaching the standard security measures used by victim organizations.
It’s unnecessary to attack directly at the point of security if hackers use supply chain attacks like this. All the MFA in the world can’t stop intruders who already have access to network environments and administrator accounts and can then forge security tokens that look legitimate to verification processes.
Supply chain complexity exponentially increases security difficulty
Today, with so many SaaS and cloud services being used by nearly every organization, the supply chain web is so complex that no single organization can perform due diligence deeply enough.
Without sufficient due diligence, organizations have unidentified gaps that leave them vulnerable to cyber attacks.
This vulnerability spans across the entire industry and many software development environments, like Orion, create security weak points because open source or reused code can bury problems quickly and without a trace.
So, what can be done?
Solutions the industry is trying to implement
Before the SolarWinds hack, the cybersecurity industry could easily see the potential for supply chain threats. But until it happened, it did not feel imminent so it didn’t actually change cybersecurity standards. Now, the largest tech players like Google and Microsoft and new cybertech innovators like NextlLevel3 are trying to develop solutions.
Some of these include:
Implementing FIDO-compliant account protection locking and policy management
Creating software “ingredient lists” to more easily check and verify code
Using cryptography for signing code in open source projects to make it more secure
Educating and improving standard security procedures like changing secrets after a breach
Increasing physical hardware security to limit attack surfaces
More closely monitoring activity, identity verification, and sign-in intent
Removing unnecessary permissions and reducing them as much as possible
Industry efforts aren’t totally there yet
Google is throwing $10 billion at the cybersecurity standards and development problem, emphasizing supply chain vulnerabilities, hoping something will stick. So are many of the other giant tech corporations.

Even the US government is getting involved with an executive order requiring federal agencies to generate guidelines, conduct evaluations, and implement improvements. But isn’t that just like the government to generate guidelines? Will these efforts be effective or are they mere handwaving?
Gaps in current solutions still leave you vulnerable
More transparency is one of the key things that is still needed across the tech world and in security solutions. If the industry ever hopes to shine a light on supply chain attacks before they reach their ultimate victims, a mindset shift has to spread industry-wide.
New solutions to validate sensitive information without exposing it need to be developed with urgency. End user and executive decision maker education also needs to catch up with current threats. Social engineering continues to target weak points in human security diligence and what most users assume is securing their activity (like MFA) is not always doing the trick.

Vulnerabilities are more often abstract
Code and software are very concrete and literal. A bug can be clearly identified and fixed. The more difficult part of improving cybersecurity standards is understanding the environment and preventing unexpected possibilities. The most effective hacks are the ones you don’t see coming. That’s why good security protects against what you can’t see by creating a philosophy of verification like zero trust, rather than simple mechanisms for verification.
Ongoing lessons from the SolarWinds hackers
Some of the most important lessons from the SolarWinds supply chain attack are still being learned:
Trojan attacks are almost impossible to spot
Supply chain vulnerabilities are expanding, not diminishing
MFA and passwordless security won’t prevent user error of forged credentials
Monitoring and verifying all activity is more important than ever
These are huge problems with difficult solutions. It can be overwhelming for any cybersecurity team to think about. But understanding where potential threats may come from and adding tools to your belt will put you ahead of many threats that other organizations have been and continue to be victimized by.
