Multi-factor authentication is great, but what happens when hackers go around it?
Multi-factor authentication (MFA) is the security standard everyone wants, but despite hopes for it to reduce risk by 90%, hackers bypass MFA regularly.
With the determination of Wile E. Coyote, attackers keep InfoSec teams speeding around like Roadrunner, trying to stay ahead of the game.
Unfortunately, not all companies are fast enough, and Coinbase learned that difficult lesson last year when 6,000 of its users had money stolen through an MFA bypass.
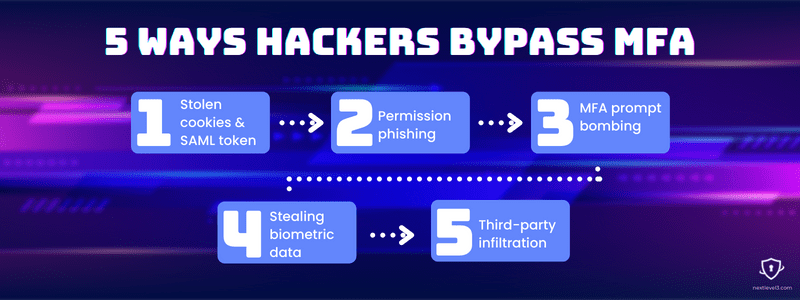
Since multi-factor authentication is important but not unbeatable, here are five ways hackers bypass MFA.
#5
Third-party infiltration

If a company has strong security measures in place already, an effective way hackers bypass MFA is through third-party applications with weaker security. These are sometimes called software supply chain attacks, and the infamous SolarWinds breach of 2020 is a prime example.
Vendors — In the case of SolarWinds, the attackers beached the software provider, creating a backdoor in one of its software updates that thousands of customers trusted and installed.
Legacy apps — Another way hackers exploit weaker security systems is through legacy apps and software that haven’t been eliminated by IT or updated with current security standards.
Recovery attempts — When users forget passwords, recovery accounts are often less secure. Many people use personal emails as a backup. With man-in-the-middle attacks, hackers can hijack the recovery process.
#4 Stealing biometric data
In 2021, researchers uncovered a Windows 10 vulnerability that allowed IR frames of people’s faces to trick facial recognition software. A USB drive with stolen biometric data or photos of people could fool the authentication process and bypass MFA, verifying fingerprints or faces without a password.
Deep fakes — In China, hackers used bootlegged images to create deep fakes of users to trick the biometric presentation attack detection (PAD) system of a government-run database and sent out fake tax invoices.
Theft and black market — Biometric data like faces, fingerprints, and voices are unchangeable, strong incentives to a hacker seeking access to a user’s personal information. Hackers bypass MFA by stealing or buying the biometric data that MFA systems ask for.
#3
MFA prompt bombing

Wearing people down or taking advantage of lowered guards is another easy way for attackers to sidestep multi-factor authentication. The Lapsus$ hacking extortion gang proved the ease of sidestepping multi-factor authentication on multiple occasions by using social engineering tactics to target human vulnerabilities.
Multiple MFA prompts — Hackers bypass MFA by sending MFA requests to users continuously until they finally accept one. Other times the prompts are less frequent but recurring until, inattentive, someone accepts.
Delayed MFA prompt — Another way to lower a user’s guard is to time an MFA prompt for morning hours when employees are likely to be logging into accounts for work, as usual, reducing the chances of suspicion.
#2 Permission phishing
There are various types of man-in-the-middle attacks that can be used for phishing. Typical ones commandeer credentials from users who think they’re entering them into the app they’re trying to log into but are actually giving it to the hacker. Permission phishing has a slight twist.
Consent — Permission phishing uses a consent agreement that looks just like the real app’s permissions requests. When a user accepts, they inadvertently grant continual access to the hacker.
One case of permission phishing gained access to Microsoft 365 email accounts. Certain apps can ask for continual access. For example, when the email app on your phone connects to your ESP. Microsoft said the breach granted “Permissions that would allow attackers to create inbox rules, read and write emails and calendar items, and read contacts.”
#1
Stolen cookies & SAML token

The infamous example of how hackers bypass MFA has been the SolarWinds hack. Combining the software supply chain attack with man-in-the-middle attacks on SolarWinds customers, hackers were able to steal keys and credential tokens that enabled them to access privileged accounts.
Golden SAML — After the SolarWinds attack, this type of token theft and forged credentialing was named the Golden SAML technique. By intercepting the authentication token, attackers can get continued access with little risk of detection because the signing token actually verifies the malicious actor.
Stealing cookies — More common man-in-the-middle attacks involve stealing a cookie from a logged-in user’s active session and obtaining access until the user is logged out. Many applications use cookies to temporarily store credentials, so users stay logged in, sometimes for up to 30 days.

Multi-factor authentication is not a silver bullet
Just about every cybersecurity service provider heralds MFA as the number one solution to threat deterrence. But increasingly, hackers bypass MFA altogether, and these five examples are just the tip of the iceberg. Keeping multi-factor authentication as part of your company’s security system is wise. But don’t be fooled into thinking that’s the end of the story.
There are hundreds of ways for threat actors to creatively maneuver their way to the crown jewels. MFA is just one important piece in a comprehensive security plan. Ensuring your vendors maintain strong perimeters, educating all internal users, a zero-trust philosophy, and, yes, multi-factor authentication are all critical elements for your InfoSec team to consider.
